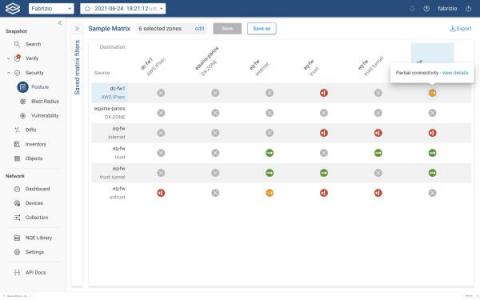
Where is Your Zone-to-Zone Connectivity Matrix?
If you’re like most of the complex IT shops we talk with, you probably don’t even have a current security matrix to store anywhere – file cabinet or data folder. The connectivity matrix is essentially the company security posture, but almost no one has a comprehensive way to visualize and easily understand the connectivity status between the various configured security policies (zone-to-zone policies).