Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Datadog
Risk Management is a Team Sport with Emilio Escobar
Demo - Prioritize Vulnerabilities that Matter
Threat modeling with Datadog Application Security Management
Threat modeling is a critical part of building high-performing, secure systems. It is responsible for “analyzing representations of a system to highlight concerns about security and privacy characteristics.”1 Creating an effective threat model involves two main steps: system modeling to map out all existing system components and the relationships between them, and threat elicitation to identify areas in the system that could be vulnerable to a security issue.
Datadog achieves ISO 27701 Processor certification for customer data privacy
With the establishment of the EU General Data Protection Regulation (GDPR) and the expanding international landscape of data protection laws, organizations today face complex requirements and heightened scrutiny when it comes to data privacy. In addition, public awareness of data exploitation and digital surveillance is growing, and individuals are more concerned than ever about data privacy.
Enhance corporate application security with AWS Verified Access and Datadog
AWS Verified Access makes it easy and more secure for organizations to grant local or remote access to corporate applications without the use of a VPN. By using Verified Access, you can assign group policies to manage your organizations’ application access and administrative privileges at scale.
State of Application Security
Web application security is an important concern for organizations. Attacks have historically happened at the infrastructure and network level, but today, they increasingly target the business logic exposed by services that handle the most critical and sensitive data. The attack surface of applications is ever increasing, with more than 25,000 vulnerabilities identified in 2022 alone.
Datadog's Security Observability Day 2023
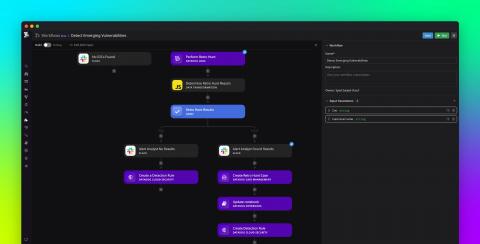
Automate common security tasks and stay ahead of threats with Datadog Workflows and Cloud SIEM
Detecting and remediating security threats is a constantly evolving concern for modern DevSecOps and security operations center (SOC) teams. Moreover, manually investigating and responding to vulnerabilities and threats is time-consuming, laborious, and knowledge-intensive.
Datadog acquires Codiga
Developers spend over a third of their time fixing bad code and reducing technical debt. Detecting and fixing errors in production is not only more costly than doing so during development but also slows down innovation and has a negative impact on productivity, the development experience, and team morale. Having tools that help catch and fix coding mistakes earlier in the development process creates a better experience and increased productivity.