Gain visibility into risks, vulnerabilities, and attacks with APM Security View
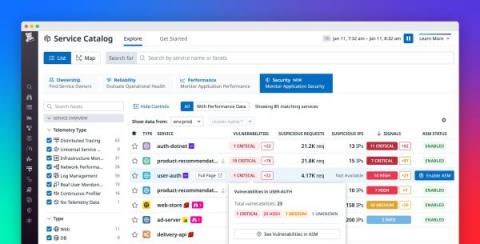
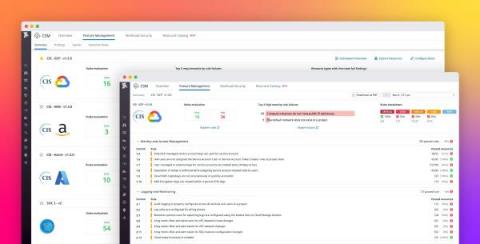
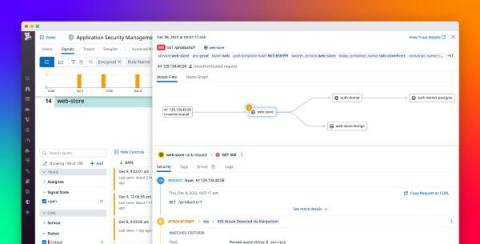
As your business grows and your services scale in number and complexity, it’s difficult to maintain a rapid pace of innovation while keeping your applications secure. It’s particularly challenging to respond to attacks, as DevOps and security teams need to collaborate to understand each attack’s root cause and remediate the vulnerabilities that enabled it.