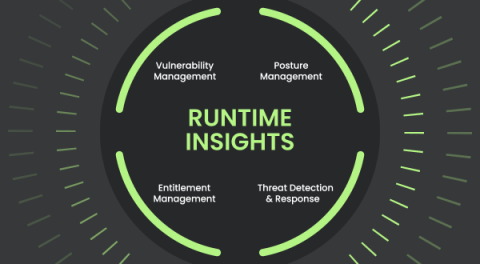
Active Cloud Risk: Why Static Checks Are Not Enough
How would you feel about your home security system if it only checked to see if your doors and windows were locked periodically? This security system would provide great visualizations of your house and how a criminal could get from one room to another, ultimately reaching one of your prized possessions, like a safe. However, it doesn’t have cameras on your doorbell or windows to alert you in real time when someone suspicious was approaching, or worse, trying to break into your house.