Look both ways: Preventing suspicious behavior with end-to-end detections
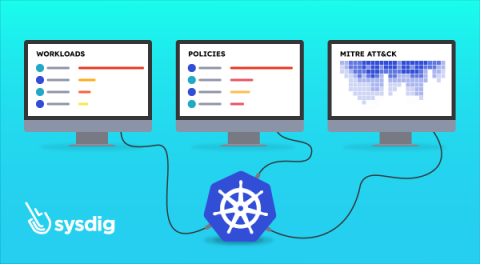
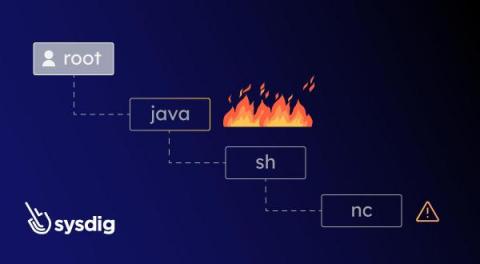
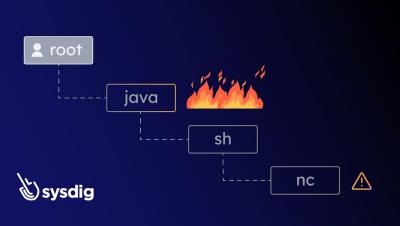
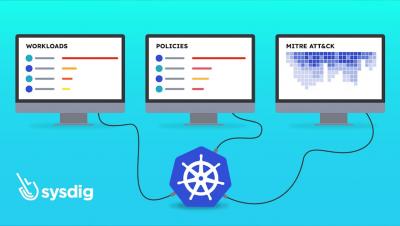
In the rapidly evolving digital landscape, malicious actors constantly adapt their strategies to infiltrate our systems. Traditional endpoint detection mechanisms are no longer sufficient to protect our applications and workloads against advanced threats. To effectively address this concern, it has become imperative to embrace a broader approach to threat detection. This entails a paradigm shift towards incorporating both agent-based and agentless detection methods.