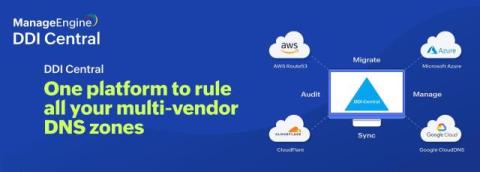
Centralize the management of zones hosted with external vendors in DDI Central
Business continuity is key for safeguarding an organization’s reputation in today’s threat-filled digital landscape, where outages and security threats are quite prevalent.