Resolve network security issues efficiently with the Firewall Analyzer-ServiceDesk Plus integration
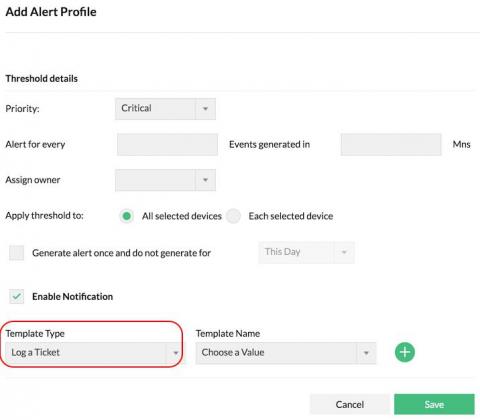
ManageEngine Firewall Analyzer reviews firewall logs to capture network security threats. It generates alerts upon detecting security threats and attacks, and notifies you, the security administrator, in real time. You can configure alerts to be sent via email, SMS, and more. With these real-time notifications, you can troubleshoot to take instant remedial action. You can also make changes to your firewall policies and configurations to prevent recurring security incidents.