Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Snyk
Stranger Danger: Your JavaScript Attack Surface Just Got Bigger
Buffer overflow attacks in C++: A hands-on guide
A buffer overflow is a type of runtime error that allows a program to write past the end of a buffer or array — hence the name overflow — and corrupt adjacent memory. Like most bugs, a buffer overflow doesn’t manifest at every program execution. Instead, the vulnerability is triggered under certain circumstances, such as unexpected user input.
Snyk Unveils Snyk Cloud, the Industry's First Developer-Centric Cloud Security Solution
Snyk Demo in 20 Minutes | 2022
Best practices for your first 30 days with Snyk
This post is applicable to Business plan and Enterprise plan customers. Adopting a new platform can seem intimidating, but with Snyk it doesn’t have to be. We have three tips to help you roll out Snyk, and have a seamless and successful first 30 days across your business or enterprise. Before you start inviting team members and importing projects, you’ll want to consider your account strategy, set up single sign-on (SSO), and configure your first organization.
Webinar recap: Snyk and the new era of software security
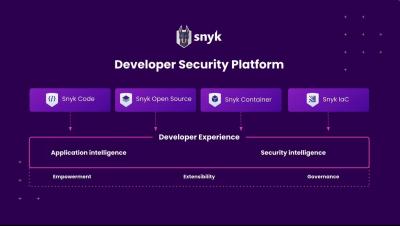
Snyk’s Senior Product Marketing Manager, Frank Fischer, recently hosted a webinar about the value in using a developer security platform to secure code, dependencies, containers, and infrastructure as code (IaC). During this talk, Fischer discussed the shift in software security that has occurred over the past decade, the need for developers to take part in the security process, and the value of Snyk in securing the entire development lifecycle.
Addressing cybersecurity challenges in open source software with the Linux Foundation
Snyk recently partnered with the Linux Foundation to produce a report focusing on the state of security in the open source software (OSS) space. The report was based on 550+ survey responses and 15 interviews with OSS maintenance and cybersecurity experts. Following the report’s publication, experts from Snyk held a webinar with the Linux Foundation to discuss some of the key insights.
Application Security 101 - What you need to know in 8 minutes
Webinar recap: The missing story with every cloud breach
Snyk’s Chief Architect, Josh Stella, recently hosted a webinar about cloud security. Stella was the co-founder and CEO of Fugue, a cloud security and compliance company that was acquired by Snyk. With the capabilities of Fugue, Snyk will bring its developer-first security platform into the cloud security space. During this talk, Stella discussed the missing story in every cloud breach: the tale of how, when, and where attackers operate in the cloud.