Identify, prioritize, and fix vulnerabilities with Reachable Vulnerabilities for GitHub
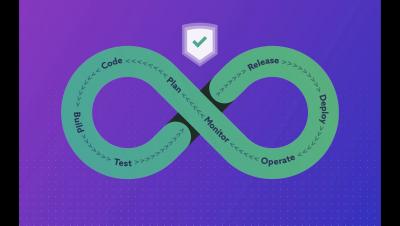
Imagine you are a Java programmer and that you just decided you want to use Snyk Open Source scanning to help you find security problems in your third party libraries. Good call! However, after connecting your repository to the Snyk Open Source scanner, you find out that you have ten or maybe even 50 vulnerabilities in the packages you depend on. The major question is: where do I start?