Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
NIST
NIST's Definition of Cloud Computing
Which NIST Framework Is Best For Your Organization?
NIST Standards and Guidelines for Enhancing Software Supply Chain Security Include Security Ratings
At SecurityScorecard, we believe that making the world a safer place means transforming how organizations view cybersecurity. For us, this means that companies must take a holistic approach, protecting systems not just from the inside, but also knowing what an organization’s vulnerabilities look like from the outside-in to see what the hackers are seeing.
Titania Launches New Module for Organizations Working with U.S. Government Agencies to Meet Cybersecurity Compliance Accurately
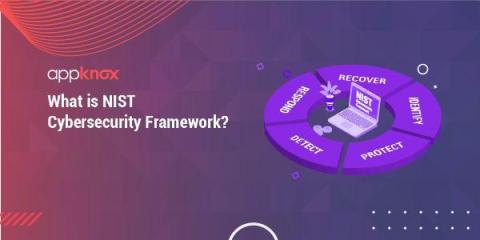
What is NIST Cybersecurity Framework? ( CSF ) | Complete Guide
NIST Cybersecurity Framework (CSF) is a voluntary security framework created through industry, academic, and US government collaboration that aims at reducing cyber risks to critical infrastructure. The framework is a result of the Presidential Executive Order (EO) 13636 that directed NIST to develop a framework in collaboration with the security stakeholders of the economic and National security of the US.
Key Takeaways From the NIST Ransomware Risk Management Profile
Ransomware groups have generated so much damage that the United States Federal government has made it a top priority to thwart such efforts including, hosting a major international summit on the topic, setting up a ransomware task force and repeatedly urging organizations to improve their cyber resilience.
Lookout is Collaborating With the U.S. Government on a New Vision for Zero Trust
In early 2020, almost every government agency embraced telework in response to the pandemic. With telework, employees operate outside the security perimeter that was put in place to protect them and the agency’s data. As a result, telework has had significant cybersecurity ramifications. Lookout has a long history of collaborating with the public sector to secure agency employees.
NIST's New Draft for Ransomware Risk Management
Cyberattacks against businesses of all sizes are at all-time highs. Data from 2021 and projections for the future of cybersecurity suggest that the frequency and intensity of these attacks will only continue to grow. At the forefront of most cyberattacks in 2020 was ransomware, a type of malicious malware attack where attackers encrypt your organization’s data and demand payment in exchange for a decryption key to restore access.