Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest Videos
Zero Standing Privileges End User Experience for AWS IAM Identity Center
In this video, we'll explore the end-user experience with standing permissions and a Zero Standing Permission (ZSP) approach, utilising a third-party Identity Provider (IdP) like Entra-ID or AzureAD.
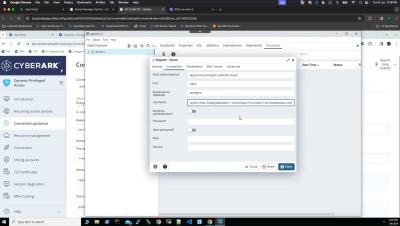
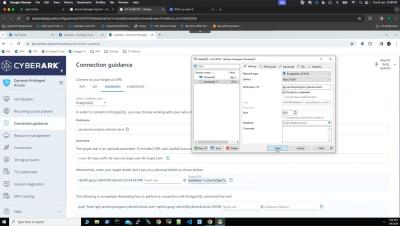
Securing Database Access: DPA Zero Standing Privilege Approach with Native pgAdmin Utility
In this video, we'll guide you through the process of utilising CyberArk DPA's capabilities to seamlessly connect to a Postgres database using the PGadmin client, leveraging the secure foundation of JIT access approach for enhanced security and efficiency.
Securing Database Access: DPA Zero Standing Privilege Approach with Native HeidiSQL Utility
In this video, we'll guide you through the process of utilizing CyberArk DPA's capabilities to seamlessly connect to a Postgres database using the HeidiSQL client, leveraging the secure foundation of JIT access approach for enhanced security and efficiency.
CyberArk Endpoint Privilege Manager & ServiceNow Integration
In this video, we delve into the seamless integration of CyberArk Endpoint Privilege Manager and ServiceNow IT Service Management. Discover how this integration streamlines and automates end user privilege elevation requests by leveraging existing ServiceNow workflows. By enhancing security measures and operational efficiency, this collaboration between CyberArk and ServiceNow marks a significant advancement in managing and securing privileged access. Watch now to learn more about this powerful integration.
Securing Database Access: DPA Vaulted Account Approach with Native PGadmin Utility
In this video, we'll guide you through the process of utilising CyberArk DPA's capabilities to seamlessly connect to a Postgres database using the PGadmin client, leveraging the secure foundation of Vaulted Accounts for enhanced security and efficiency.
Securing Database Access: DPA Vaulted Account Approach with Native HeidiSQL Utility
In this video, we'll guide you through the process of utilising CyberArk DPA's capabilities to seamlessly connect to a Postgres database using the HeidiSQL client, leveraging the secure foundation of Vaulted Accounts for enhanced security and efficiency.
CyberArk SCA Slack Workflow Approval (Part 2)
In part 2 of this video, we will go over the CyberArk SCA Slack workflow approval process.
CNBC TV18 Host Gautam Srinivasan speaks with CyberArk Regional Director Rohan Vaidya
CNBC TV18 Host Gautam Srinivasan speaks with CyberArk Regional Director Rohan Vaidya on the critical role of digital identity in the face of unauthorized access.
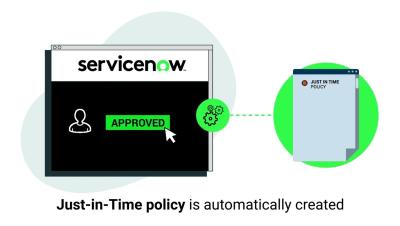
Streamlining Secure Cloud Access Requests with ServiceNow
Join Eva as she seamlessly navigates through Secure Cloud Access request workflows, showcasing just-in-time privilege creation and simplified policy management. See how Eva requests and obtains "PowerUserAccess," with Analucia efficiently managing approvals in ServiceNow.