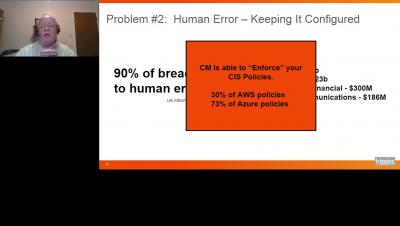
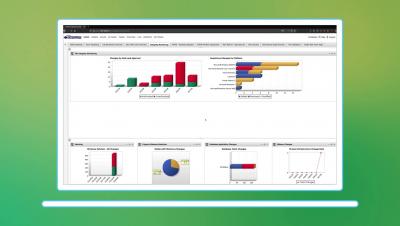
Tripwire ExpertOps: Managed Cybersecurity and Compliance
Welcome to Tripwire's Security-as-a-Service solution. Tripwire® ExpertOps extends your staff with experienced security professionals who leverage your in-house team. You’ll see rapid time to value with your choice of multiple services that can reduce your security risks and simplify your policy compliance—all hosted on a cloud infrastructure. Tripwire ExpertOps includes software, ongoing consulting, professional services, and cloud infrastructure in a single subscription.