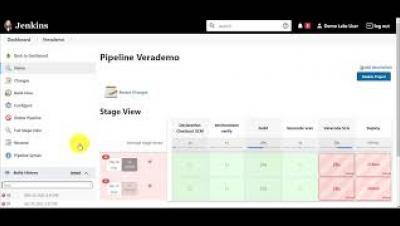
Use the Jenkins Credentials Binding Plugin to Protect Your Veracode Credentials
In this video, you will learn how to: You can use the Jenkins Credentials Binding Plugin to hide your Veracode API credentials from the Jenkins interface and logs. You use the plugin to associate, or bind, your Veracode API credentials to environment variables and save them to the Jenkins credentials store. During a build, Jenkins uses the environment variables to secretly access your credentials. The Jenkins interface and logs only show the bound environment variables.