Top Data Tokenization Tools of 2024: A Comprehensive Guide for Data Security
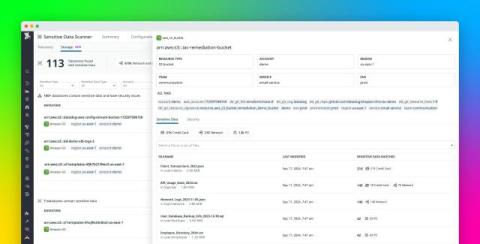
Data tokenization is a critical technique for securing sensitive information by substituting it with non-sensitive tokens. This process plays a crucial role in data protection, especially in industries handling large volumes of personal or financial information. Here, we explore the top data tokenization tools of 2024 to help organizations find the right solutions for protecting their data.