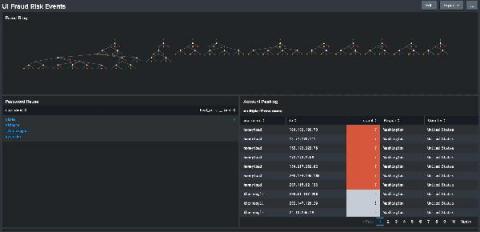
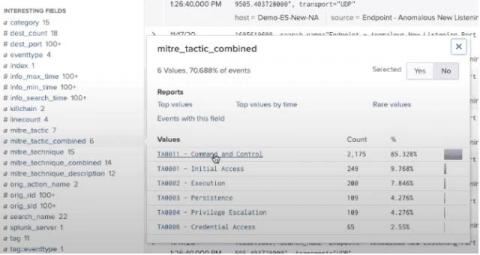
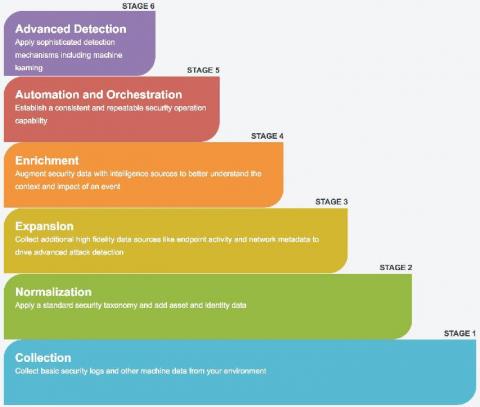
Next Level Automation: What's New with Splunk Phantom
Splunk Phantom 4.10 introduced many new enhancements, including the ability to develop playbooks in Python 3. In fact, Python 3 is now the default for Splunk Phantom playbooks. In doing so, we needed to create two different “playbook runners” to ensure we could continue to support playbooks written in Python 2.7 while also supporting Python 3.