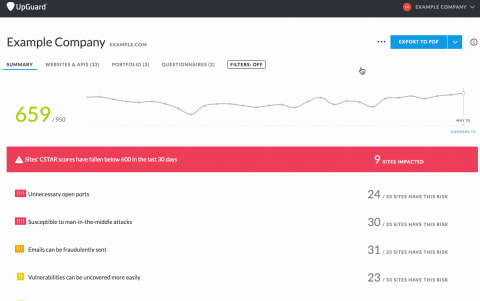
UpGuard Tasks: a Lightweight Tracking System for Ops
It's not pleasant to think about, but the fact is that when we go to work we are expected to do things. But what are the things that need doing? If we can answer that question without hours of meetings or dozens of emails we can finish our work and do...other things. UpGuard's new Tasks feature provides a lightweight project management system designed especially to maintain quality in a rapidly changing environment.