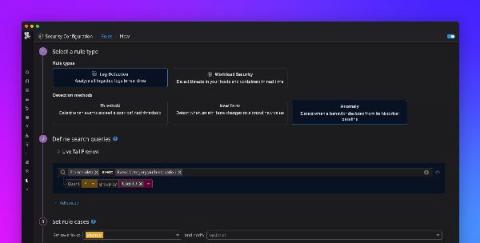
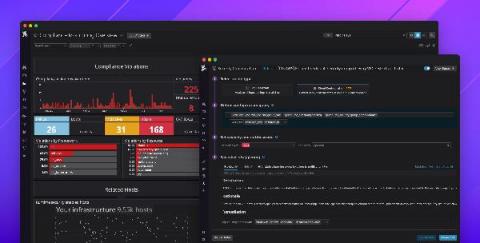
Detect security threats with anomaly detection rules
Securing your environment requires being able to quickly detect abnormal activity that could represent a threat. But today’s modern cloud infrastructure is large, complex, and can generate vast volumes of logs. This makes it difficult to determine what activity is normal and harder to identify anomalous behavior. Now, in addition to threshold and new term –based Threat Detection Rules , Datadog Security Monitoring provides the ability to create anomaly