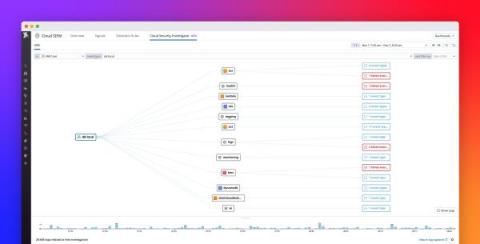
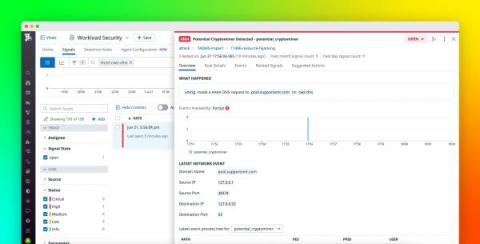
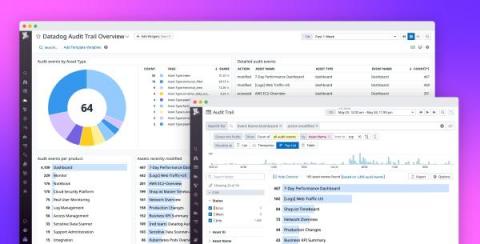
Visualize activity in your cloud environment with Datadog Cloud SIEM Investigator
Investigating the origin of activity in cloud-native infrastructure—and understanding which activity is a potential threat—can be a challenging, time-consuming task for organizations. Cloud environments are complex by nature, comprising thousands of ephemeral, interconnected resources that generate large volumes of alerts, logs, metrics, and other data at any given time.