Challenges Facing Sensitive Sectors in Working Securely from Home
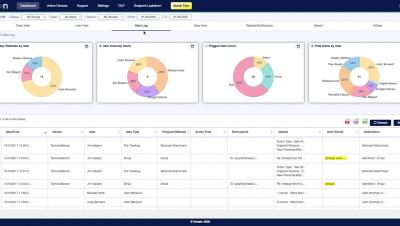
Making the transition to a work from home arrangement has been a heavy lift for a lot of organizations. However, due to various risk factors and regulations, making the sudden shift to working from home has been more complicated for some sectors than others. Industries such as the financial and healthcare sectors, as well as those working for the government, face tighter restrictions on how they are allowed to work remotely.