How Time, Entitlements and Approvals (TEA) Can Secure the Keys to Your Cloud
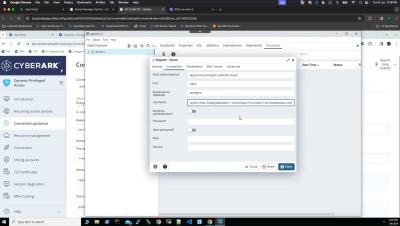
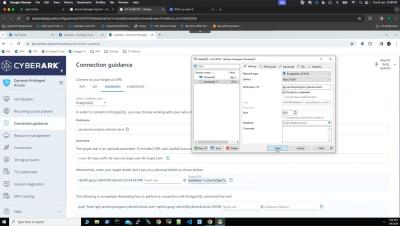
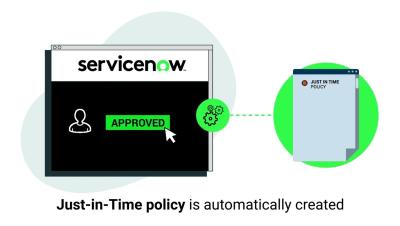
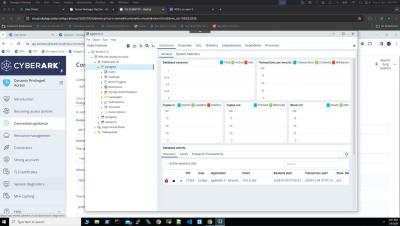
A popular topic of conversation in my day-to-day work is how to secure privileged access to cloud management consoles and workloads. And that’s no surprise, considering more and more applications and workloads are migrating to the cloud. Up until recently, the answer has typically been clear when it comes to identity security and privileged access management (PAM). It’s simple: first, you manage credentials by securing them in a vault. The next step is to rotate them.