The Unseen Risks of Open Source Dependencies: The Case of an Abandoned Name
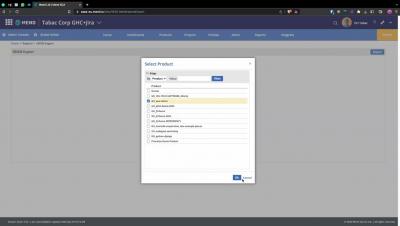
One often-overlooked risk in the bustling ecosystem of open-source software are vulnerabilities introduced through software dependencies. We mention this because today, a malicious actor took over a RubyGems package name with more than two million downloads. Mend.io technology detected the package before it could be used for an attack, but the case of ‘gemnasium-gitlab-service‘ serves as an important reminder of the risk of neglecting dependency management.