Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
April 2021
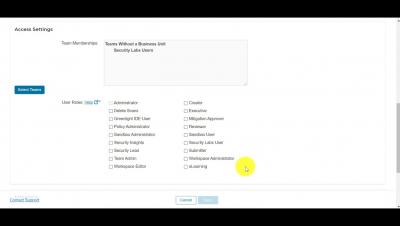
Create Security Labs Users from the Veracode Platform
Executive Order on Cybersecurity Is Imminent: It's Been a Long Time Coming
Following President Biden’s address to Congress last night in which he referenced cybersecurity as a priority twice, news is circulating today that the executive order on cybersecurity is imminent. This news comes as a much awaited and long overdue step towards creating standardization and structure around cybersecurity.
Developer Training Checklist: 5 Best Practices
The role of the developer has evolved over the past several years. Developers are not only responsible for writing code and releasing new software rapidly but also for securing code. By implementing security in the software development lifecycle, you can reduce risk and cost without slowing down time to production. But the developer role is already stretched so thin and many developers don’t have a background in security.
How a Microsoft Engineer Implemented Veracode for a Large Azure Project
With the need to produce innovative software faster than ever, and cyberattacks not slowing down, it’s no surprise that, for projects large and small, ensuring the security of your code at every step is key. But if software engineers want to meet these everyday demands with success, it’s important to understand how different security scanning types fit in throughout the development process, and how the needs of your team might impact scans.
Are You Targeting These Risky Red Zone Vulnerabilities?
Modern software development is full of security risk. Factors like lingering security debt, insecure open source libraries, and irregular scanning cadences can all impact how many flaws dawdle in your code, leading to higher rates of dangerous bugs in susceptible and popular languages.
Practical Steps for Fixing Flaws and Creating Fewer Vulnerabilities
All security flaws should be fixed, right? In an ideal world, yes, all security flaws should be fixed as soon as they’re discovered. But for most organizations, fixing all security flaws isn’t feasible. A practical step your organization can – and should – take is to prioritize which flaws should be fixed first.
Reporting Live From Collision Conference 2021: Part Two!
If you caught part one of our recap series on this year’s Collision conference, you know we covered a roundtable talk hosted by Veracode’s own Chris Wysopal. The talk focused on the risks of AI and machine learning, delving into discussions of how to manage the security aspects of these future-ready technologies — especially when it comes down to consumer privacy.
Reporting Live From Collision Conference 2021: Part One!
This week, Collision (virtually) kicked off its annual conference, bringing together creatives, builders, influencers, innovators, and other great minds to cover some of the hottest topics in business and technology. Known as ‘America’s fastest-growing tech conference,’ this year Collision featured over 450 speakers with more than 100 hours of content to consume across the three-day event.
Access and Navigate the Veracode Security Labs Interface
View and Filter Labs in Veracode Security Labs
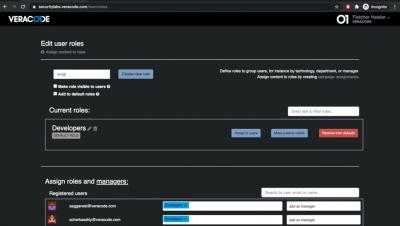
Edit and Assign Security Labs Roles to Users
Create a Campaign and Assign Content to Roles in Security Labs
Add and View Due Dates for Assignments in Security Labs
View and Report on User Progress in the Veracode Security Labs Reporting Page
Customize Lab Content in Veracode Security Labs
DevSecOps in Practice: How to Embed Security into the DevOps Lifecycle
You’ve heard of DevOps. And by now, you’ve probably also heard of DevSecOps, which extends DevOps principles into the realm of security. In DevSecOps, security breaks out of its “silo” and becomes a core part of the DevOps lifecycle. That, at least, is the theory behind DevSecOps. What’s often more challenging for developers to figure out is how to apply DevSecOps in practice. Which tools and processes actually operationalize DevSecOps?
The First Step to Achieving DevSecOps Is Shifting Security Culture Left
To achieve DevSecOps you need to shift security left. Sounds simple, right? Well, it’s easier said than done. A recent survey conducted by SANS Institute found that 74 percent of organizations are deploying software changes more than once per month – an increase in velocity of nearly 14 percent over the past four years. To release software monthly, weekly, or even daily, security has to be integrated into the development process, not tacked on at the end.
The Biggest Breaches and Data Leaks of 2020
Year after year, cyberattackers cause unnecessary stress for organizations, disrupting innovation and impacting profit. 2020 was no different – last year brought a bevy of damaging breaches that cost organizations precious money and time they couldn’t get back. Ranging from thousands to billions of records exposed, breaches big and small gave threat actors access to sensitive information like email addresses, locations, passwords, dates of birth, and more.
DevSecOps and the Cloud: How Leaning on Your Cloud Provider Can Help You Shift Left
Over the past several years, an increasing amount of organizations have been moving their applications from on-premises to cloud-hosted platforms. And with the current pandemic forcing most businesses to adopt a fully remote work environment, the cloud is even more appealing. Gartner reported that cloud spend rose by double digits in 2020, and it’s expected to continue to grow by 18.4 percent in 2021.
Technology Companies Have the Largest Proportion of Applications With High-Severity Flaws
As a result of the worldwide pandemic, technology companies were forced to pivot to fully remote operations. For many organizations, this meant accelerating their digital transformation efforts. But despite the investment in digital transformation efforts, there haven’t been enough investments in security measures.
Password Storage Using Java
This is the eighth entry in the blog series on using Java Cryptography securely. The first few entries talked about architectural details, Cryptographically Secure Random Number Generators, encryption/decryption, and message digests. Later we looked at What’s New in the latest Java version. All of this equipped us to talk in detail about some of the most common Cryptographic applications. We started by looking at the symmetric cryptography-based application with Message Authentication Code.
Veracode Launches Technology Alliance Program
University of Warwick Wins Veracode's First-Ever Hacker Games
AppSec with LolCats: Click2Cat - the Security Extension to Veracode You Didn't Realize You Needed
Fixing security findings in your code can be hard. Sometimes you need help from other developers who have solved these problems before. Veracode provides one-on-one time with ex-developers who can coach you through different approaches to address security findings. But sometimes, you don’t really want advice. Instead, you need a boost to help you get through the day of reducing risk in your software.
Secure Coding Urban Myths and Their Realities
“Science and technology revolutionize our lives, but memory, tradition, and myth frame our response.” – Author Arthur M. Schlesinger Urban myths rely on their communities of origin to thrive and survive.