Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
April 2022
What does XDR mean for your organization?
Sidecars for network monitoring
Monitoring container traffic and extracting rich security-centric metadata provides SOC analysts an inviolable source of truth for threat detection and incident investigation. This data complements the deep visibility provided by container agents and broad visibility through monitoring audit logs.
Detecting Windows NFS Portmap vulnerabilities
This month, Microsoft announced two vulnerabilities in portmap, which is part of ONC RPC, on Windows systems. This blog will discuss Zeek detection packages for CVE-2022-24491 and CVE-2022-24497 developed by Corelight Labs.
Network Evidence For XDR
Explore Corelight evidence in Humio Community Edition
Now available: A free and easy way to learn about Humio and Corelight. As part of our alliance partnership with CrowdStrike and Humio, Corelight is excited to announce a new collaboration that allows our customers and the community to experience the value of evidence.
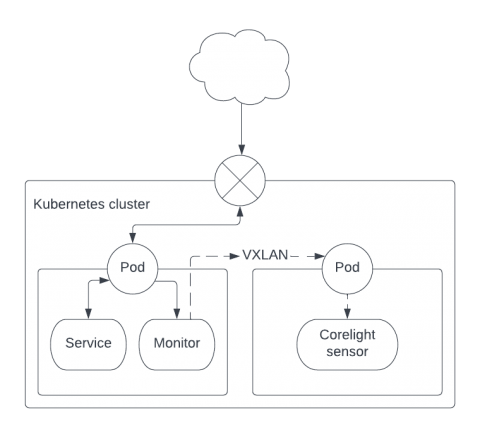
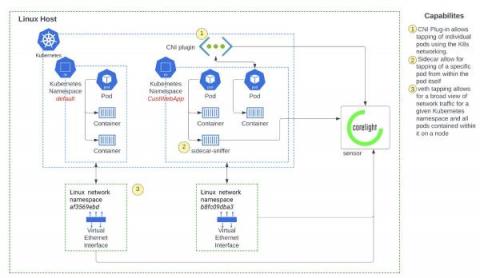
Deeper visibility into Kubernetes environments with network monitoring
Network monitoring solutions can overcome the security visibility blind spots in Kubernetes environments, by providing a source of truth for SOC analysts. Container security solutions broadly span the spectrum of (a) prevention - securing the container image and ensuring the right policies are in place during runtime and (b) detection - monitoring runtime events for threat detection and investigation.
Don't trust. Verify with evidence.
What matters most in a criminal trial? Evidence. Everything depends on the quality and depth of facts deployed to build a case for innocence or guilt. Without compelling evidence, no jury can draw accurate conclusions.