Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
January 2022
What a Modern Privileged Access Management (PAM) Solution for Cloud-Native Applications Looks Like
Privileged Access Management (PAM) is a go-to solution to prevent privilege misuse and insider threats, and limit malware propagation. After all, properly protecting and monitoring the keys to the kingdom is always a good practice. Privileged Access Management has been even more critical in recent times. With the advent of the cloud where infrastructure is provisioned with a single API call and authenticated with a single API key, the risk of someone misusing these credentials is far higher.
Enabling compliance for database access
Moving fast, and meeting HIPAA compliance with Teleport
How Dylan Statmat of https://www.verticalchange.com/ uses Teleport to obtain HIPAA compliance.
How to Keep Your Cloud Infrastructure Secure and Compliant
Unifying AWS IAM Access Across Multiple AWS Accounts and Products
AWS Identity and Access Management (IAM) is a keystone to accessing AWS accounts, but as companies grow, it can be difficult to understand and standardize, especially across many AWS accounts. To put some personality into the challenges of managing identity for multiple AWS resources and accounts, I’ll start with a short story about a fictional company that you might recognize as similar to the one you work in today! ACME Net is growing fast.
Securely accessing clinical data without a VPN
How Teleport eliminated password procedures at thredUp
How Roman Chepurnyi uses Teleport to eliminate passwords at https://www.thredup.com/
How to Use SSH Agent Safely
The SSH agent (ssh-agent) is an SSH key manager that stores the SSH key in a process memory so that users can log into SSH servers without having to type the key’s passphrase every time they authenticate with the server. In addition to the key management feature, SSH agent supports agent forwarding, which helps to authenticate with servers that sit behind a bastion or jump server.
Securing a World of Physically Capable Computers with Bruce Schneier
Using Z3 Theorem Prover to analyze RBAC
Z3 is a satisfiability modulo theories (SMT) solver developed by Microsoft Research. With a description like that, you’d expect it to be restricted to esoteric corners of the computerized mathematics world, but it has made impressive inroads addressing conventional software engineering needs: analyzing network ACLs and firewalls in Microsoft Azure, for example.
Identity-Based Access for SSH
Lack of access accountability and unmonitored access create a considerable security risk for organizations, and the best way to mitigate this challenge is by implementing identity-based access.
SSH Hardening Tips to Prevent Brute-Force Attacks
SSH servers are a common target for brute-force attacks. This is even more true if your infrastructure sits behind an SSH bastion because attackers have no choice but to compromise the bastion host either by exploitation or denial of service. In this article, we will list a few controls which will help you harden your SSH servers from brute- force attacks.
SSH Bastion Host Best Practices
SSH bastion hosts are an indispensable security enforcement stack for secure infrastructure access. Every security compliance standard that deals with remote infrastructure access (e.g., FedRAMP AC-17 - Remote Access, HIPAA §164.312(a)(1) - Access control, SOC2 CC6.1 - Manage Points of Access) mandates preventing direct network access to the servers and APIs.
Why Financial Services Companies That Value Agility & Security Pick Teleport
2022 feels a little different, doesn’t it? Every day I’m prepared to hear something new, something scary, or something exciting. These last couple of years have made it seem like we just never know what is coming next. It’s no different for financial services companies who have to be prepared for the unexpected, including disruptive technologies that can challenge their core businesses.
What You Need to Know About Adding a SaaS Component to Your Hardware or Software Business
Many market-leading companies who have dominated their respective sectors with hardware or on-prem/installable software solutions are turning to SaaS offerings to fuel the next phase of their growth. Why? Simple. Market valuations are much higher for SaaS companies than they are for traditional software and hardware companies. The median multiple on earnings for a SaaS company is 12.7x as of Q3 2021 according to venture capitalist Jamin Ball who tracks the Public Cloud Software (e.g.
RFDiscussion - Teleport Desktop Access
How to Set Up Two-Factor Authentication for SSH
One way to enhance SSH login security is by using two-factor authentication (2FA). This approach forces an administrator to self-identify with an additional security verification in addition to the local admin credentials. This tutorial guides you through setting up Google Authenticator PAM to enable 2FA for users connecting to SSH on a Linux server. We’ll use nano as our editor in examples.
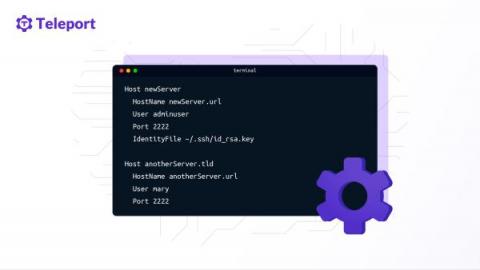
SSH Client Config Files and How to Use Them
SSH client configuration files allow us to connect to servers with pre-configured commands. This saves typing each SSH command parameter when logging into a remote machine and executing commands on a remote device. This article will examine secure shell (SSH) client configuration (config) files and their functions. Specifically, we will show an example of an SSH client config file to learn how to use these files before creating an example config file that connects to a fictitious server.
5 Best Practices for Securing SSH
Strictly following security best practices is the first step to cybersecurity. Although SSH is the industry standard for both security and efficacy for remote server access, as with any software, SSH is only as secure as configurations applied to the server and client configurations. In this article, we’ll explore five SSH best practices you should observe to boost the security of your infrastructure.
Tracking Changes with SSH Audit Logging
Audit logging for SSH is essential for system security, and it’s often an important part of compliance regulations. Developers and administrators should only be granted access to the resources they need, and a continuous monitoring system should be in place to ensure that they aren’t abusing that access.