Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
September 2021
Panel on Shift Level with CISO's Part - 2
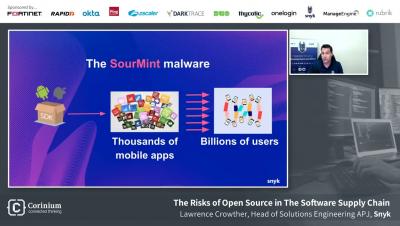
The Risks of Open Source in the Software Supply Chain with Lawrence Crowther, Snyk
Python security best practices cheat sheet
In 2019, Snyk released its first Python cheat sheet. Since then, many aspects of Python security have changed. Using our learnings as a developer security company — as well as Python-specific best practices — we compiled this updated cheat sheet to make sure you keep your Python code secure. And before going any further, I need to give special thanks to Chibo and Daniel for their help with this cheat sheet!
Snyk Container registry security integrations extended to GitHub, GitLab, Nexus, DigitalOcean, and more
We’re excited to share that you can now use Snyk Container to scan container images stored in many more container registries. The latest additions include Github Container Registry, Nexus, DigitalOcean, GitLab Container Registry, and Google Artifact Registry.
Snyk Customer Story - Expel
Snyk Code CLI support now in public beta
Snyk is on the mission to make Static Application Security Testing (SAST) tools work for developers throughout the DevOps pipeline. Snyk Code scans in real time with high accuracy — and it does it right from the tools and workflows developers are already using. For example, the IDE plugins for IntelliJ, PyCharm, WebStorm, and Visual Studio Code make it easy to code, scan and fix even before code hits the version management.
The Tokenised Auth
DevSecOps Road Trip Germany stop - Sven Ruppert & Mathias Conradt
Introducing the new Snyk Docs Portal and Support Portal
We’re excited to announce two big updates to our Snyk User Content platform. You can now get better, quicker, clearer access to Snyk user documentation, allowing you to find the information you need, to get more and better use of your Snyk platform. This will help you implement, enable, and configure your Snyk integration, leading to a faster and smoother adoption and usage of Snyk at your company. Here are the enhancements to our User Content platform.
DevSecOps Road Trip France stop - Smaïne Kahlouch, Mathieu Gillot, Tanguy Combe & Ismael Hommani
DevSecOps Road Trip Netherlands stop - Nanne Baars & Brian Vermeer
Learning Equality Micro-interview with Snyk Impact
Fast Forward Micro-interview with Snyk Impact
Develop for Good Micro-interview with Snyk Impact
CareerVillage.org Micro-interview with Snyk Impact
AIEDU Micro-interview with Snyk Impact
UPchieve Micro-interview with Snyk Impact
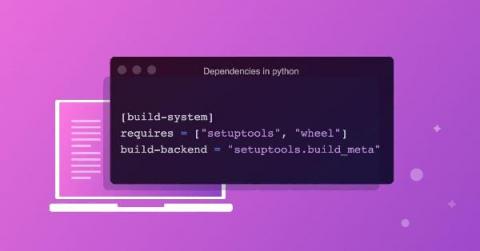
A (soft) introduction to Python dependency management
Python has been deemed as a “simple” language — easy to use and easy to develop scripts to do numerous tasks — from web scraping to automation to building large-scale web applications and even performing data science. However, dependencies are managed quite differently in Python than in other languages, and the myriad options of setting up an environment and package managers only add to the confusion.
DevSecOps Road Trip UK stop - Andrew Martin & Lili Kastilio
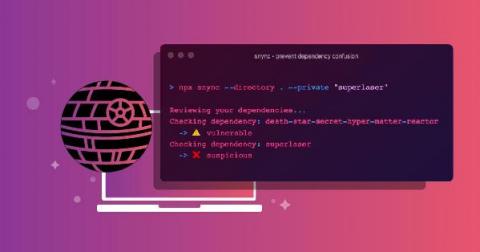
Detect and prevent dependency confusion attacks on npm to maintain supply chain security
On February 9, 2021, Alex Birsan disclosed his aptly named security research, dependency confusion. In his disclosure, he describes how a novel supply chain attack that exploits misconfiguration by developers, as well as design flaws of numerous package managers in the open source language-based software ecosystems, allowed him to gain access and exfiltrate data from companies such as Yelp, Tesla, Apple, Microsoft, and others.
Dev-first SAST: Increase your developer productivity while staying secure
Snyk Closes $530 Million Series F Investment at $8.5 Billion Valuation
The inevitability of Developer Security
It’s exciting to share the news of our new funding round. It let us bring onboard some amazing investors and funds for further growth, along with setting the company valuation at $8.5B — a pretty big number. When you look at this valuation, and consider these smart investors expect it to grow substantially, you may wonder — how can this market be big enough to support these numbers? I would say the real question is — how can it not be?
Announcing Snyk's Series F: Leading the World to Developer Security
Snyk Code support for PHP vulnerability scanning enters beta
Snyk Code support for PHP vulnerability scanning is now available in beta. Now security issues in PHP code can be identified quickly and easily. To get started, log into Snyk or sign up for a free account. Once logged in on the dashboard, click on the Add Project button in the top right corner and connect to a repository you want to scan.
7 steps to improve developer security
Empathy — that ability to understand what others are feeling — might be the secret ingredient when it comes to successfully shifting security into the developer world. Snyk co-founder and president Guy Podjarny hosts The Secure Developer podcast, and in interview after interview, guests have repeatedly spoken about how empathy, understanding, and a bias toward action are the biggest components of a successful developer-first security culture.