Empowering Teams for Better Security: A Conversation with Jigar Shah - Secrets of AppSec Champions
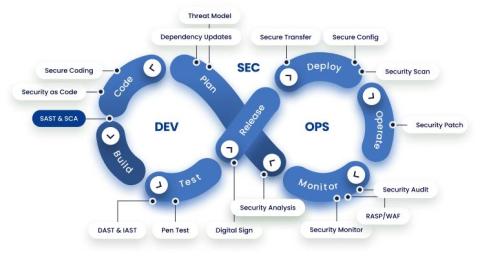
Developing a Security Culture: In today's highly digital and interconnected world, cybersecurity isn't just an IT issue; it's everyone's responsibility. Creating a robust security culture within your organization involves integrating security awareness into your daily operations. Train your employees, provide adequate resources, and define clear roles and responsibilities for security champions and influencers.