Application Security - The Complete Guide
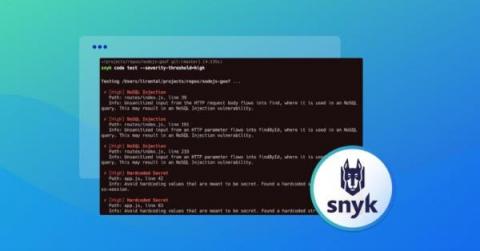
Application security is an essential part of the software development lifecycle, and getting it right should be a top priority in today’s ever-evolving and expanding digital ecosystem. Application security is the practice of protecting your applications from malicious attacks by detecting and fixing security weaknesses in your applications’ code.