Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
One Identity
Identity Manager | Update 9.x #2 | Connected System Module Enhancements
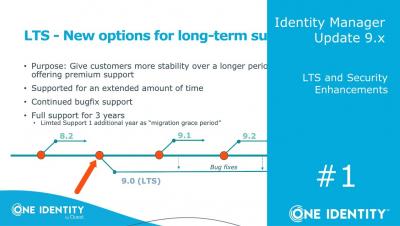
Identity Manager | Update 9.x #1 | LTS and Security Enhancements
Identity Manager | Angular Web Development #12 | Modifying the Standard Web Portal #6
How to conduct a Privileged Access Management risk assessment
In today's business landscape, organizations rely heavily on digital systems, applications, and webpages for their daily operations. However, with the increasing use of technology comes growing risks of unauthorized access to sensitive information and data.
Identity Manager | Angular Web Development #12 | Modifying the Standard Web Portal #6
Identity fatigue - the security challenge that threatens identity processes and systems
There’s a new cybersecurity challenge threatening the identity processes and systems of organizations worldwide: identity fatigue.
Identity Manager | Angular Web Development #11 | Modifying the Standard Web Portal #5
Best practices for implementing Privileged Access Management
Privileged Access Management (PAM) is a critical component of any organization's cybersecurity strategy. Privileged accounts provide access to the most sensitive data and systems within an organization. As such, it's essential to manage them carefully to prevent unauthorized access, data breaches and cyberattacks. Here are some best practices for implementing PAM in your organization to ensure that your privileged accounts are secure and protected.