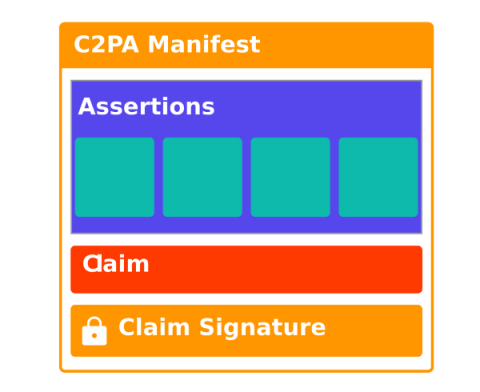
Creating a better internet at IETF117
The other week in San Francisco at IETF117, a group of developers and subject matter experts gathered to do just that. The IETF mission is: “To make the internet work better by producing high quality, relevant technical documents that influence the way people design, use, and manage the internet.” This standards body is quite unique – anyone with the right passion can join. Believe it or not, humming is a measure of consensus.