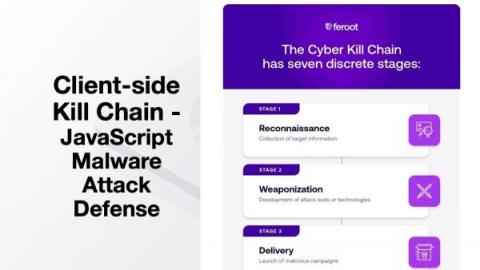
Client-Side Kill Chain: JavaScript Security Attack Defense
In my decade working in the cybersecurity industry, I’ve developed quite a few fond memories learning from talented security professionals. In 2015, I found myself working with Andy Pendergast at ThreatConnect. (As a little background, Andy is one of the fine folks who developed the Diamond Model for Intrusion Analysis. He is considered to be a veritable cybersecurity encyclopedia among his peers.) At the time, I was new to cyber threat intelligence (CTI).