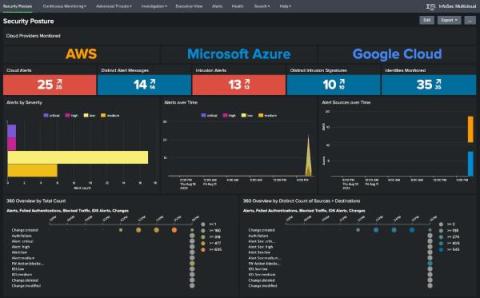
Splunk Named #1 SIEM Provider in the 2022 IDC Market Share for SIEM for 3rd Time in a Row
Splunk has been named #1 SIEM Provider in the Worldwide Security Information and Event Management Market Shares, 2022: The Multitude of SIEMs (doc #US51012523, July 2023). The continued recognition from IDC as a SIEM market Leader is a testament to our commitment to delivering a data-centric, modern solution that delivers data-driven insights for full-breadth visibility for our users.