Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Teleport
Infosec for startups
Ghosts of Past Employees
This blog post started as a seasonal message from our Newsletter. We’ve expanded it to be appropriate for the rest of the year. With more employees changing jobs in 2021 than ever before, there are likely to be a few skeletons in the closet.
An Engineer's Perspective on Onboarding
Before I joined the security industry, I was an end user. Coming in with that first-hand experience equips me to talk about secure remote access from multiple perspectives: as a vendor and as a practitioner. This lets me see the technologies available and also understand the drivers and issues engineering orgs face adopting them, particularly with onboarding engineers. I’ve been a support engineer for over 20 years, across Operations and System & Database Administration.
Running IT at a Hyper Growth Startup
At Teleport we do IT a little differently — supporting a global remote company in hypergrowth is no easy feat and the playbook is different from traditional IT work. In this article, we want to share some of our IT philosophies that enable our employees to keep their agility despite working very asynchronously around the world.
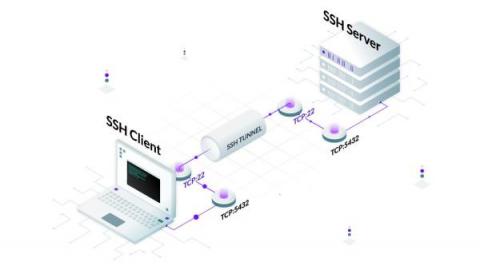
SSH Tunneling Explained
Although the typical use case of SSH is to access a remote server securely, you can also transfer files, forward local and remote ports, mount remote directories, redirect GUI, or even proxy arbitrary traffic (need I say SSH is awesome?). And this is just a small set of what’s possible with SSH.
Securing Internal Applications
When should a startup call the FBI
Build vs Buy for Start-ups
This is the age-old question faced by so many tech teams: do we build or buy a system we need? TL:DR, Buying can save your engineer time for building the core stack and for the fun experiments needed to determine when to shake up the core stack.