Privacy, SSE Adoption: My Takeaways From the 2022 Gartner SRM in London
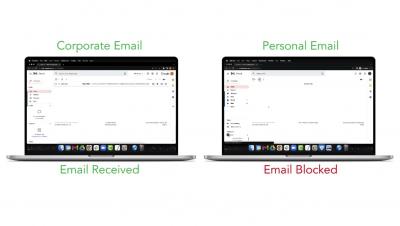
After a two-year hiatus, the Gartner Security and Risk Management, London is back! I had the privilege of attending a number of sessions, spending time talking with analysts and digesting some of the latest cybersecurity trends and strategies, including the Top Cybersecurity Predictions for 2022-2023 from Gartner. Two themes that stood out to me were security service edge (SSE) and extended detection and response (XDR) Below are some of my key takeaways from this year’s conference.