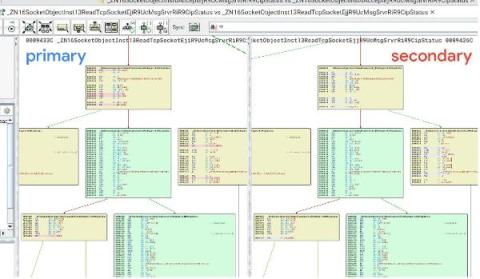
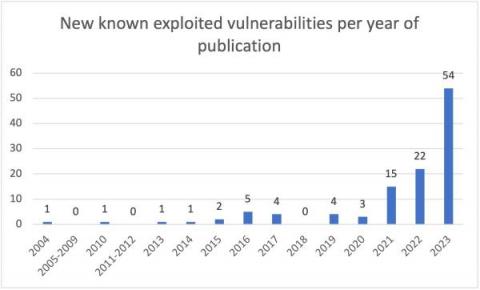
Hacktivists attack U.S. water treatment plant - analysis and implications
Almost a year ago to the day, on December 1 2022, Forescout Vedere Labs published a report detailing several hacktivist operations that targeted critical infrastructure in response to the Russian invasion of Ukraine and other geopolitical developments. Since the most recent chapter in the Hamas-Israel conflict started on October 7, there have been multiple similar claims of attacks from hacktivists taking opposing sides in the conflict.