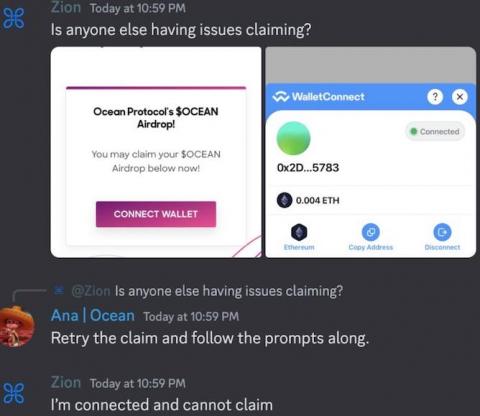
New Cryptocurrency Coinbase Phishing Campaign Uses Social Engineering
A phishing campaign is impersonating cryptocurrency trading platform Coinbase, Tech.co reports. Crypto trader Jacob Canfield described the campaign in a Twitter thread, stating that the threat actors texted and then called him.