Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
ManageEngine
ManageEngine Log360 named in GigaOm radar report on automated security operations management (ASOM)
ManageEngine Log360 was featured in the GigaOm Radar report on Automated Security Operations Management (ASOM), published in October 2022 and written by Logan Andrew Green. The research firm’s report includes an in-depth study of the solutions offered by some of the major vendors in the market and highlights Log360 as a Challenger in the ASOM sector. Log360 is a unified SIEM solution from ManageEngine with integrated DLP and CASB capabilities.
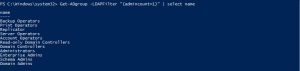
Monitoring domain user accounts with elevated access rights
3Standard users having elevated privileges is never good news. Accounts such as domain admins, enterprise admins, schema operators, krbtgt, administrators, and replicators, are a few privileged user groups within an Active Directory (AD) environment. The AdminCount attribute is an AD attribute set to “1” on privileged user accounts.
Five worthy reads: Why should we worry about cyberwarfare in 2023?
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. In this edition, we’ll explain why cyberwarfare could be a potential cyberthreat in 2023. Cyberwarfare was one of the top trending terms in 2022, and the incidents that happened last year have opened up more discussions regarding this topic. Most people think cyberwarfare is synonymous with the term cyberwar.
Audit domain controller logon activity: ADAudit Plus User Logon report
ManageEngine ADAudit Plus is a UBA-driven auditor that bolsters your Active Directory (AD) security infrastructure. With over 250 built-in reports, it provides you with granular insights into what’s happening within your AD, such as all the changes made to objects and their attributes. This can include changes to users, computers, groups, network shares, and more.
Secure your organization with just-in-time access
Just-in-time (JIT) access is a cybersecurity feature where users, applications, or systems are granted access to resources only when needed and for a limited time. This approach limits the risk of privileged accounts gaining unauthorized access to sensitive data. JIT access is often used in conjunction with other security measures—such as multi-factor authentication and encryption—to provide a strong, layered defense against threats.
Look twice before you "LookBack"
What makes great art, whether it be in literature, painting, film, or photography, so challenging and valuable that it seems to be out of our realm of understanding? In any such art, there is more to it than meets the eye. Whether these artists hid some messages for the generations in their art is beyond our knowledge. As the world transitioned into the digital age, we began to use this technique to communicate a lot of information in a single image.
Audit your users' logons: ADAudit Plus User Logon report
ManageEngine ADAudit Plus is a UBA-driven auditor that fortifies your Active Directory (AD) security infrastructure. With over 250 built-in reports, it provides you with granular insights into what’s happening within your AD, such as all changes made to objects and their attributes. This can include changes to users, computers, groups, network shares, and more.
Threat detection review: Insider threats in cybersecurity
Globally, 67% of companies experience between 21 to 40 insider-related incidents per year, according to Ponemon Institute’s The Cost of Insider Threats 2022 report. The same report reveals that the frequency and cost of insider attacks have increased significantly over the past two years. Insider threats are one of the tougher attacks to predict and prevent, because of the difficulty in identifying insiders.