Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Threat Intelligence
The state of the SOC: skills shortages, automation and gaining context remain a challenge for SOCs
The security operations center (SOC) has been on the front line facing the pandemic-induced escalation of cybersecurity threats in the past eighteen months. A 2020 study by Forrester found that the average security operations team receives more than 11,000 alerts per day and that figure is likely to have grown in the intervening period. While they were deeply engaged responding to the crisis, SOC teams were simultaneously facing the disruption common to all formerly office-based workers.
Threat Advisory: STRT-TA02 - Destructive Software
The Splunk Threat Research Team is monitoring open channel intelligence and government alerts indicating the possibility of malicious campaigns using destructive software in relation to ongoing geopolitical events. Based on historical data of named geopolitical actors, the use of destructive payloads has been observed in past campaigns.
Simplify Your Journey to SOC Modernization
The discipline of threat intelligence began to be incorporated in cyber defense processes within private sector companies nearly a decade ago. Over the past few years, more and more organizations began to establish their own threat intelligence operations, building Security Operations Centers (SOCs), incident response (IR) capabilities and threat intelligence teams.
Threat intelligence outlook 2022: what we can learn from the past year
Power the SOC of the Future with the DataLinq Engine - Part 3
In my first blog in this three-part series, we discussed the importance of data to the modern SOC, and the unique approach of ThreatQ DataLinq Engine to connect the dots across all data sources, tools and teams to accelerate detection, investigation and response.
Power the SOC of the Future with the DataLinq Engine - Part 2
In my first blog in this series, we discussed the importance of data to the modern SOC, and the unique approach of ThreatQ DataLinq Engine to connect the dots across all data sources, tools and teams to accelerate detection, investigation and response. We developed the DataLinq Engine with the specific goal of optimizing the process of making sense out of data in order to reduce the unnecessary volume and resulting burden.
The University of New Orleans: Protecting The Future
Power the SOC of the Future with the DataLinq Engine - Part 1
Evidence continues to mount that it isn’t a matter of if, but when and how an organization will be attacked. So, we are seeing Security Operations Centers (SOCs) narrow the focus of their mission to become detection and response organizations. As they look to address additional use cases, including threat detection and monitoring, investigation, incident response and hunting, data becomes incredibly more important.
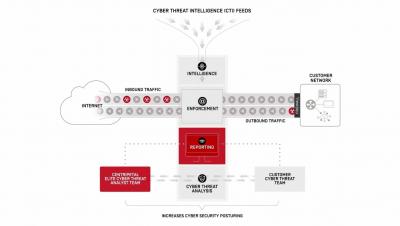
A Year of Threat Intel: Looking Back at SpiderLabs Research in 2021
2021 will go down in the record book as another critical year in the cybersecurity sector, with high-profile ransomware campaigns and supply chain attacks making national headlines. The elite Trustwave SpiderLabs team was in the trenches for our clients around the world -- providing key insights, threat intelligence, and breakthrough research on a wide array of vulnerabilities and malware. Take a journey through some of the most-read research from Trustwave SpiderLabs in 2021.