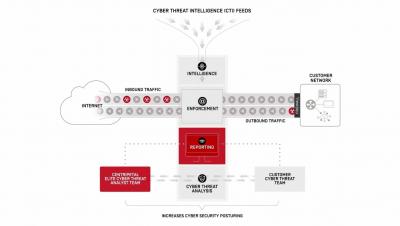
Combat Advanced Threats with a Multi-disciplinary Threat Intelligence Program
Ransomware attacks on Colonial Pipeline, JBS Foods and Kronos are just a few recent examples in the rise of cyber-physical attacks that disrupt lives of individuals and have the potential to cause physical harm. This concerning trend is capturing the attention of organizations worldwide, with Gartner predicting that 75% of CEOs will be personally liable for cyber-physical security incidents by 2024.