Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Logging
Importing Logs from FluentD into Falcon LogScale
One of the primary debugging tools for a cloud-native developer is the simple, humble log file. Some malfunctioning systems can be impossible to debug without them. FluentD is an open source log collector that provides unified log processing across multiple emitter systems, either on the same logical device or separate devices. For example, on a single k8s pod, logs are emitted from the pod itself, the container running in the pod and the microservice running in the container.
How to Inspire Privacy Best Practices Throughout Your Organization
In our post-pandemic world, more and more individuals are splitting their time between the corporate office and their home office or working remotely full-time. This shift is blurring the lines between professional and personal cyber hygiene and privacy, which can pose a significant risk to organizations.
The Ethical Hacking Guide: Hacking for Security
Companies are under more threat than ever. The rise in cyber threats is alarming: 2021 saw a 30% increase in cyberattacks compared with 2020. Even sophisticated systems with complex countermeasure technologies for security may be vulnerable to attack. Many organizations turn to hackers to counteract these threats. Ethical hackers use the tools and methods of malicious actors to help companies pinpoint their weaknesses and build a more resilient and secure system.
Shift Left Security: How To Shift Security Left for Software Development
For a long time, security and development were two distinct aspects of programming. As organizations started to leverage software and technology as differentiating factors, the speed and quality of development became more important than ever. Organizations no longer had time after development was complete to address security vulnerabilities. Catching vulnerabilities too late opens companies up to unnecessary risk and can be costly to fix.
Importing Logs from Logstash into Falcon LogScale
Logging is an important tool in the cloud developer’s toolbox. It can be the critical component used to discover why your authentication service can’t connect to its database or why your API gateway is not routing upstream traffic correctly. Today, humans are not the only ones reading logs. Machines are also participating in the logging landscape by helping identify patterns (and outliers) in your system logs.
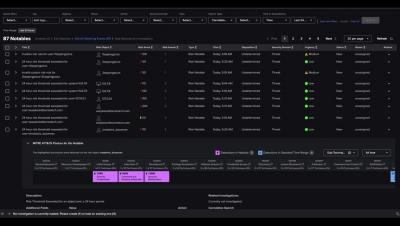
SIEM In Seconds - Splunk ES Overview - MITRE ATT&CK Framework
Putting the 'E' in Team: Solution Integration Enablement for Security Build Motion Partners
I am sure many of you have heard the term “cybersecurity is a team sport.” If you haven’t, I say get on the right team. Security is a complex, ever-changing game of skill and preparedness (never chance). As we like to say here at Splunk, it is all about cyber resilience. To best be prepared to win this game, we need the best team. As with any team sport, there really needs to be other teams - after all what fun is it playing by yourself?
SIEM Tools: Which Vendors Should Be on Your List?
Whether your organization is ready to deploy its first security information and event management (SIEM) solution or you’re looking to upgrade to a modern, next-gen SIEM, the number and types of tools available in the market can be overwhelming. This post will help you choose the right vendor and best SIEM tools for your business needs. SIEM tools have been available for about 15 years, but like most technologies, there has been a great deal of evolution and innovation over that time.
From Registry With Love: Malware Registry Abuses
The Windows Registry is one of the most powerful Windows operating system features that can tweak or manipulate Windows policies and low-level configuration settings. Because of this capability, most malware or adversaries abuse this hierarchical database to perform malicious tasks on a victim host or environment. Over the last 2 years, the Splunk Threat Research Team has analyzed and reverse engineered some of the most prevalent and successful malware families.