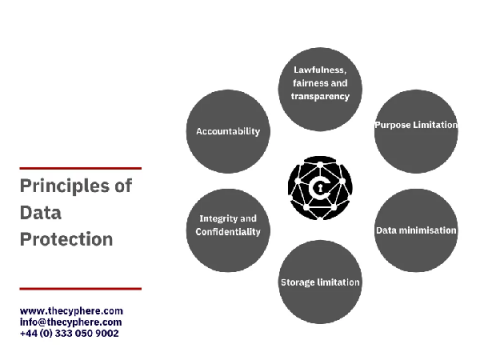
What is Data Protection by Design?
‘Privacy by design’, or as it’s now known, ‘data protection by design and default’, refers to Article 25 of the UK GDPR. This principle makes it a legal obligation for controllers to implement organisational controls which ensure data protection issues are addressed at the design stage of any project. But what does the regulation mean when it refers to organisational controls?