Introduction to JFrog Xray
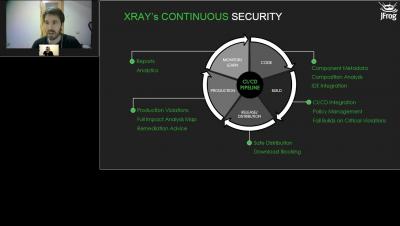
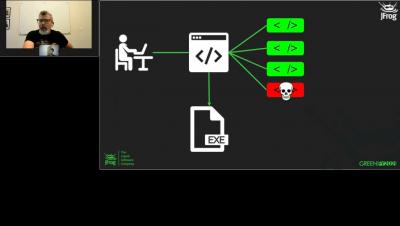
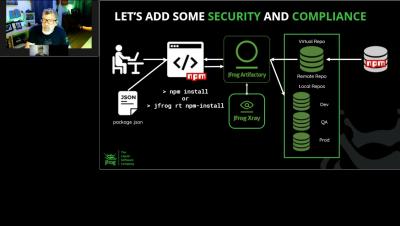
JFrog Xray is a universal software composition analysis (SCA) solution that natively integrates with Artifactory as part of the JFrog Platform. Xray gives developers and DevSecOps teams an easy way to proactively identify open source vulnerabilities and license compliance violations before they manifest in production.