Secrets Detection JFrog Security Workshop
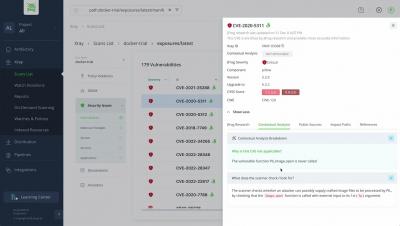
In today's software development world, developers rely on numerous secrets, including API keys, credentials, and passwords to facilitate seamless interaction between application components as they code. Failing to remove these secrets can have disastrous consequences for businesses, making it essential to find and fix them before release.