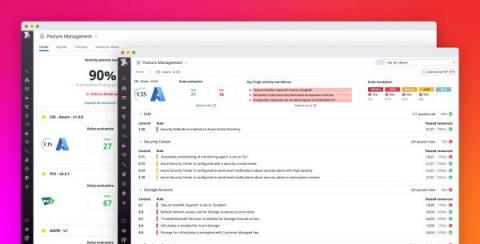
Monitor the security and compliance posture of your Azure environment with Datadog
Governance, risk, and compliance (GRC) management presents some unique challenges for organizations that deploy a myriad of cloud resources, services, and accounts. Simple misconfigurations in any of these assets can lead to a serious data breach, and compliance issues become even more prevalent as organizations try to inventory and manage assets across multiple cloud platforms and security and auditing tools.