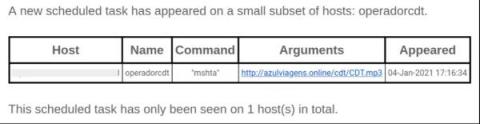
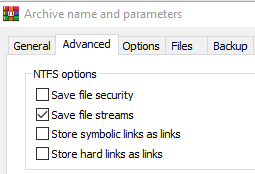
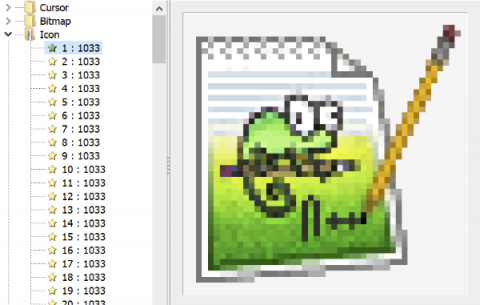
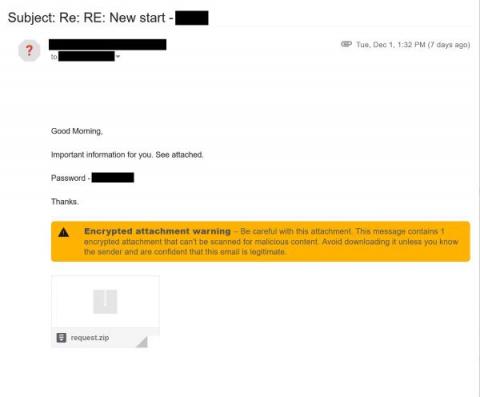
The Tactics and Techniques of Mid-Tier Adversaries, Described in 3 Attacks
When it comes to cyber security, attackers seem to be classified as terrifying Advanced Persistent Threats (APTs) or trivialised as Script Kiddies. However, more often than not, the attackers that are actually faced lie somewhere in the middle; the not-so-advanced yet somewhat-persistent threat. Their attacks are often detected but can be difficult to unravel. Their Tactics, Techniques and Procedures do not include any zero-days, but still they manage to show ingenuity.