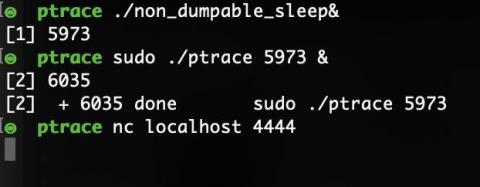
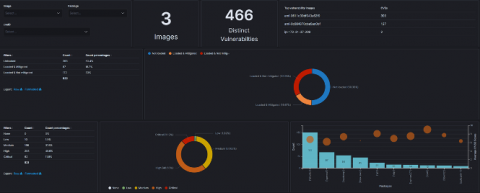
DevSecOps' Security Ownership Problem
Who’s responsible for security? Milton Friedman once said “When everybody owns something, nobody owns it, and nobody has a direct interest in maintaining or improving its condition.” While that quote was about physical buildings 40 years ago, it’s still relevant to how we build software today. The technology required to shift security left exists but the organizational shifts are lagging behind.