FedRAMP Certification: The 'New Normal' for Public Sector Agencies?
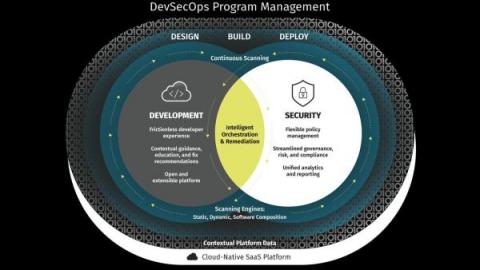
In the realm of cloud security, public sector agencies have a lot on their plates. From keeping up with the barrage of constantly emerging security guidelines (see below) to the ongoing demands of maintaining software security, the pressure on the government to lock down cybersecurity is immense.