log4jShell - Do you know what you don't know?
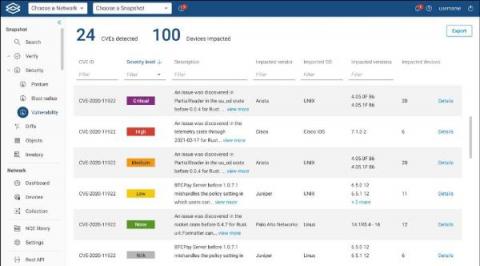
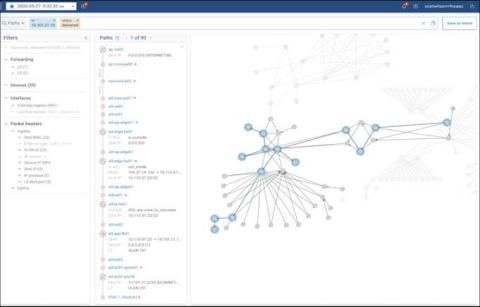
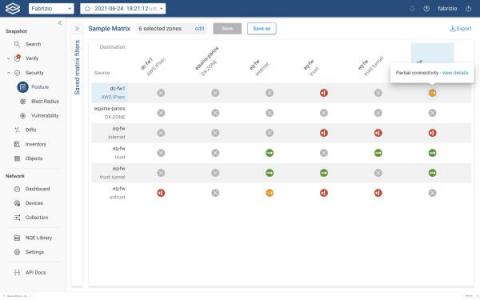
Is it just me or is the announcement of a significant CVE becoming a holiday tradition? Discovered on December 9, 2021 by Minecraft players, the Apache Log4Shell vulnerability is a uniquely insidious because it infects servers which are traditionally well insulated from attacks and perceived as unreachable by an intruder and not at risk for CVEs. Log4Shell is an entirely different can of works that proves this assumption wrong.