Building Efficient SecOps Pipelines with AWS Security Lake and Torq
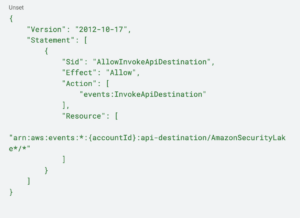
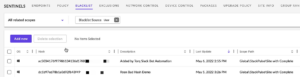
Amazon Security Lake automatically centralizes an organization’s security data from cloud, on-premises, and custom sources it into a purpose-built data lake stored in a customer’s AWS account. Amazon Security Lake reduces the complexity and costs for customers to make their security solutions data accessible to address a variety of security use cases such as threat detection, investigation, and incident response.