Detect and Respond to Threats Faster with Torq and Anvilogic
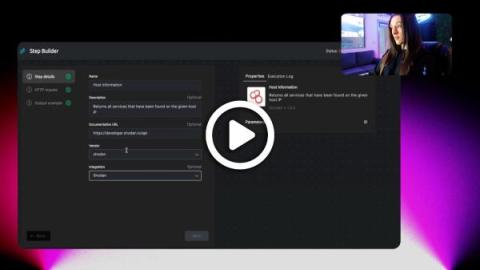
Is SIEM lock-in preventing the transformational impact of Torq Hyperautomation? Due to cost and scale challenges, endpoint activity, cloud telemetry, and network flows are often missing from detection and security automation. For security teams that keep these and other large datasets outside their SIEM, Anvilogic has teamed up with Torq to take SOC automation to the next level.